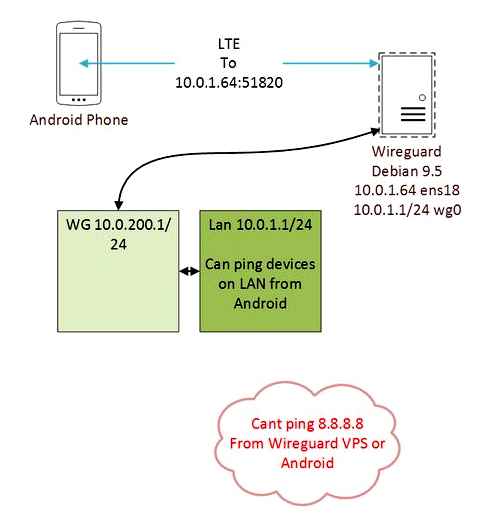
Wireguard Android does not work Internet. Several customers.
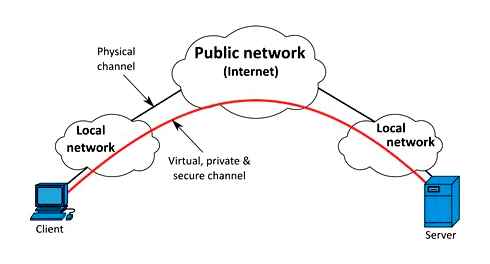
We build a VPN tunnel into a local network using Wireguard
Safe remote access to services in the local network.
VPN (English. Virtual Private Network, “Virtual Private Network”). a generalized name of technologies that allow you to provide one or more network connections (logical network) on top of another network (for example, Internet).
The most popular open source solutions for building virtual private networks are OpenVPN and IPSEC. Into the release of Linux 5 nucleus.6, which took place on March 30, 2020, has entered another implementation of VPN technology. “Wireguard”. This is a young gaining project.
In this instructions, we will configure the VPN tunnel to the local network using Wireguard and provide access from the Internet to LAN nodes from various devices.
Address in LAN. 192.168.100.0/24, VPN networks will set the range 10.0.0.0/24.
VPS will be required to place the server. When choosing, you need to pay attention to the technology of virtualization: preferably KVM, you can Xen, but OpenVZ should be avoided. The fact is that in Wireguard it is implemented as a nuclear module, and in Openvz the nucleus is very old. I will use the cheapest virtual server with the Ubuntu 20 operating system.04 (KVM 512 MB RAM 20 GB SSD 1 CPU. This configuration is quite suitable).
We will log in to the server with the rights of the ROOT user and fulfill the following commands:
# Install Wireguard Apt Update Apt Upgrade Aptall Wireguard # allowing Echo packages “NET.IPV4.IP_Forward = 1 ” /etc /sysctl.Conf Sysctl.P # We generate keys for the server: WG Genkey | Tee/etc/wireguard/private | Wg PubKey | Tee/etc/wireguard/publickey
Create a configuration file/etc/wireguard/wg0.Conf with the following contents:
[Interface] Address = 10.0.0.1/24 Postup = iptables.A forward.I %I.J Accept; iptables.T NAT.A postrouting.o eth0.J Masquarade PostDown = Iptables.D Forward.I %I.J Accept; iptables.T NAT.D Postrauting.o eth0.J Masquarade ListenPort = 51820 PrivateKey =
Postup/postdown parameters contain the IPTables rules that will be applied when starting/stopping the service. Pay attention to the name of the network intese. it must correspond to the public adapter, in my case it is ETH0. You can display a list of adapters with a team:
Select from the list the one that corresponds to the external IP address is replaced by the contents of the file/etc/wireguard/private.
Launch the VPN service and add it to the auto load:
Свой VPN на WireGuard за 5 минут. инструкция как установить на виртуальный сервер
We will make sure that the service has started correctly:
[Email Protected]:/etc/wireguard# wg Show WG0 Interface: WG0 Public: Private Key: (Hidden) Listening Port: 51820
If your router supports Wireguard (Zyxel Keeneticos = 3.3, Mikrotik Routeros = 7.1beta2, Openwrt)-you can configure the VPN client right on it. I will use Ubuntu 20 server for this purpose.04 (local address 192.168.100.7).
The first stage of setting is similar to the configuration of the server part. We carry out with the rights of a ROOT user:
# Install Wireguard Apt Update Apt Upgrade Aptall Wireguard # allowing Echo packages “NET.IPV4.IP_Forward = 1 ” /etc /sysctl.Conf Sysctl.P # We generate keys for the client WG Genkey | Tee/etc/wireguard/private | Wg PubKey | Tee/etc/wireguard/publickey
[Interface] PrivateKey = Address = 10.0.0.2/32 Postup = iptables.A forward.I %I.J Accept; iptables.T NAT.A postrouting.o WLP2S0.J Masquarade PostDown = Iptables.D Forward.I %I.J Accept; iptables.T NAT.D Postrauting.o WLP2S0.J Masquarade [Peer] Publickey = Endpoint =: 51820 Allowedips = 10.0.0.0/24 Persistentkeepalive = 20
-We replace the contents/etc/wireguard/privateKey,-/etc/wireguard/publickey from the server,-external IP address of the server. IPTABles rules in Postup/PostDown are necessary so that our client acts as a gateway in LAN. We indicate in the rules the network intese to which the local address is assigned (192.168.100.7, in my case it is WLP2S0). Check it by execution of the team:
In the Allowedips parameter, addresses are set, the routing to which will be carried out through a VPN-interacter. In the Persistentkeepalive field. the frequency of checking the accessibility of the connection in seconds. We start the service and add to the auto load:
On the server, add to the file/etc/wireguard/wg0.Conf block:
Where./etc/wireguard/public client client. We will restart the service and make sure that everything is configured correctly:
Systemctl Restart [email Protected] [email protected]:/etc/wireguard# wg show wg0 inteface: WG0 PUBLIC: Private Key: (Hidden) Listening Port: 51820 Peeer: Endpoint:: 42946 ALLED.0.0.2/32, 192.168.100.0/24 Latest Handshake: 2 Minutes, 8 Seconds Ago Transfer: 3.24 Kib Receved, 828 b Sent [email Protected]:/etc/wireguard# Ping.C 3 10.0.0.2 Ping 10.0.0.2 (10.0.0.2) 56 (84) Bytes of Data. 64 Bytes from 10.0.0.2: icmp_seq = 1 ttl = 64 time = 31.1 MS 64 Bytes from 10.0.0.2: icmp_seq = 2 ttl = 64 time = 120 ms 64 Bytes from 10.0.0.2: icmp_seq = 3 ttl = 64 time = 40.9 ms. ten.0.0.2 Ping Statistics. 3 Packets Transmitted, 3 Receved, 0% Packet Loss, Time 2002MS RTT Min/AVG/MAX/MDEV = 31.093/63.987/119.950/39.774 ms [email protected]:/etc/wireguard# ping.C 3 192.168.100.5 Ping 192.168.100.5 (192.168.100.5) 56 (84) Bytes of Data. 64 Bytes from 192.168.100.5: icmp_seq = 1 ttl = 63 time = 31.8 MS 64 Bytes from 192.168.100.5: icmp_seq = 2 ttl = 63 time = 119 ms 64 bytes from 192 192.168.100.5: icmp_seq = 3 ttl = 63 time = 40.0 ms. 192.168.100.5 Ping Statistics. 3 Packets Transmitted, 3 Receved, 0% Packet Loss, Time 2002MS RTT Min/AVG/MAX/MDEV = 31.834/63.573/118.915/39.273 ms
[Email Protected]:/etc/wireguard# wg show wg0 inteface: WG0 Public Key: Private Key: (Hidden) Listening Port: 42946 Peer: Endpoint:: 51820 Allowed IPS: 10.0.0.0/24 Latest Handshake: 8 Seconds Ago Transfer: 21.34 Kib Receved, 83.03 Kib Sent Persistent Keepalive: EVERY 21 Seconds [Email Protected]:/etc/wireguard# Ping.C 3 10.0.0.1 Ping 10.0.0.1 (10.0.0.1) 56 (84) Bytes of Data. 64 Bytes from 10.0.0.1: icmp_seq = 1 ttl = 64 time = 32.0 ms 64 Bytes from 10.0.0.1: icmp_seq = 2 ttl = 64 time = 32.6 MS 64 Bytes from 10.0.0.1: icmp_seq = 3 ttl = 64 time = 32.2 ms. ten.0.0.1 Ping Statistics. 3 Packets Transmitted, 3 Receved, 0% Packet Loss, Time 5MS RTT MIN/AVG/MAX/MDEV = 32.013/32.265/32.586/0.316 ms
Wireguard assemblies are available for the main platforms: Linux, Windows, Mac, Android, FreeBSD, Openwrt, etc. Consider the setting up of the VPN client on desktops running Linux and Windows, as well as on the Android Smartphone.
Wireguard server.
Preparation and installation.
To get started, we connect the Epel and Rpmfusion Free repositories. We attach available updates and launch a system with a new core.
Next, put everything you need on the server and collect the module for Wireguard. After, we are convinced that the module is launched into work:
The conclusion of the last team will be something like this:
Server Tuning.
We generate the keys for the client and the server:
As a result, here we get four files. a private and public key for the server, and similar to the client, which we will connect.
Create a configuration file for server/etc/wireguard/wg0.Conf with the following contents:
Of course, instead of server_private_key and client_public_key, we prescribe the keys from the files created earlier. Further, Комментарии и мнения владельцев on the config:
Address. WG0 virtual integration address on the server. Listenport. the port on which VPN will work. Allowedips. virtual IP customers who will connect to our server.
If necessary, we can also specify the parameters of Postup and postdown. the commands that will be made when the integration is turned on and off.
Client Wireguard.
We write config.
Based on the settings made, we write a simple config for the client. This config is suitable for both the desktop and for, for example, Android applications:
In this case, instead of client_private_key and server_public_key, we again substitute the keys generated earlier, and instead of server_real_ip, we prescribe the IP address of our server, on which VPN is installed.
Wireguard and desktop client.
-Create the directory /etc /wireguard, and in it we save our configuration file under the name WG0.client.ConfTry to connect to the server using WG-Quick:
Check the connection, and if everything is done correctly, then our entire traffic will now pass through the VPN server.
To disconnect from the VPN, we just execute the WG-Quick Down WG0-CLEENT command:
If necessary, we can manage the service via Systemd:
Wireguard on Android.
To use Wireguard on Android, just download the client from the Play Market or from the F-Droid repository, and just make the import of the prepared WG config for the client to connect.
And, in fact, everything. So, very simple (much easier than the same OpenVPN) we can configure the protected VPN tunnel and use it in everyday work.
Basic settings of the Vireguard VPN server
Create a directory for Wireguard:
Now you can start generating keys for the client and server:
# WG Genkey | Tee Server-Private.Key | WG PubKey Server-Public.Key # Wg Genkey | TEE Client-Private.Key | WG PubKey Client-Public.Key # Chmod 600./-private.Key
As a result of the execution of previous commands, 4 files with keys will appear: private and public keys for the server, as well as similar keys for the client (we will use them when setting up the client Wireguard).
Notes of IT specialist
Considering Wireguard settings in our previous materials, we intentionally did not touch Mikrotik, planning a separate article for this. And for this there are reasons. Routeros, under the control of which these devices work, has its own characteristics and approaches to configuration, uninteresting to other readers. And for users Mikrotik will be better if everything you need will be in one article. At the same time, we mean that the administrator working with ROS has a higher level of preparation and has the basics of networks, so we will not explain simple settings, but focus on wireguard.
You can learn how to configure Mikrotik from scratch or systematize existing knowledge in an in.depth course in administering Mikrotik. The author of the course, the certified Mikrotik coach Dmitry Skoronov personally checks laboratory work and controls the progress of each of his students. Three times more information than in the vendor program of MTCNA, more than 20 hours of practice and access.
If you are interested in the Wireguard theme in a wider one, exclusively Mikrotik equipment, we recommend reading our materials:
The following very important point: Wireguard is available only in the version of Routeros 7, which, despite the status of Stable, still has enough “childhood diseases” and other problems, so you should not go to a new version without a thoughtful analysis of all the pros and cons, as well as preliminary testing.
In our case, ChR with Routeros 7 will be used.2.1 running in the virtual machine of our test laboratory.
As we have already said, Wireguard. This is a simple tunnel without maintaining a state, the concept of a client and server are not applicable to it, each wireguard node is able to connect to other nodes and accept the connections itself. correctly call the network nodes. Feasts (Peer). initiator and responder. The first initiates the connection, the second accepts it. Although even among professionals, the terms of the client and the server continue to be applied to Wireguard nodes, the first is connected, the second accepts the connection. There is no big trouble in this, but you must understand that any wireguard node is able to perform both roles at the same time.
Mikrotik as a responder (server)
A new menu item appeared in Routeros 7. Wireguard, we go into it to the bookmark of the same name and create a new intese. We fill out the fields of NAME and Listen Port, their purpose is understandable, we advise you to use the meaningful names of the Inte Wees so that you can understand why one or another is intended. Keys will be created automatically.
If you prefer to work in the terminal, then complete the command:
Then we will assign the created IP address intended, for which let’s go to IP. Addresses and just add the right address.
Or:
Also, do not forget to allow incoming connections to the port specified when creating the Inte Wee, in our case 34567. This can be done in IP. Firewall. Filter Rules adding the rule: chain. Input, Protocol. UDP, DST. Port. 34567, in. Interface. Ether1. In its quality, the external router integration should be indicated. Action can not be chosen, since by default. Accept.
This rule should be placed before prohibiting to take incoming connections on the external integration.
In order for other nodes to be connected to our router, you need to create a feast for each of them, for this we return to Wireguard. PEERS and create a new entry. Here we need an open feast key, which should be added to the Public Key field and indicate the allowed networks in Allowed Address. In our case, we will implement a remote access or unification scenario, so we indicate there the internal address in Wireguard network, which we highlighted the feast and the network after it.
In the terminal:
Then we assign the address to the Interais if all your nodes are. then appoint yourself, if you connect to someone else’s responder, then enter the address issued by its administrator. This action is carried out in IP. Addresses.
This is an action in the terminal:
So that our router can connect somewhere, we must create a feast again. In Wireguard Feast. This is just the second side of the tunnel and it doesn’t matter we connect to it, or it is to us. In any case, we should have an integration. Our side, and feast. opposite side.
We go to Wireguard. PEERS and create a new feast, there will be more settings here, indicate: Interface. The integration we created, Public Key. A public key of a responder, we get from the other side, Endpoint and Endpoint port. Responder address and its port, Allowed Address. 0.0.0.0/0. t.e. We allow any traffic in the tunnel. If you are for NAT, be sure to add the Persistent Keepalive option, the recommended value. 25 seconds.
The terminal also has a fairly long team:
If we want to direct the entire Internet traffic to the tunnel, then we need to change the zero route, it would seem that everything is simple, but we will not rush. We pay attention to the flags of the current route: DAD. Dynamic, active, obtained by DHCP, you can, of course, turn off the receipt of routes in the DHCP client, but we will go the other way.
Recall that if several routes lead to one goal, then the one who has the narrowest mask will be selected. Therefore, instead of one zero route, add two to networks 0.0.0.0/1 and 128.0.0.0/1.
In the terminal, execute two commands:
Everything seems to be done correctly, but the Internet has stopped working. What happened? We have just wrapped all outgoing traffic in the tunnel, including our VPN server, of course, that the connection will be impossible.
Therefore, we add another route to the responder through the main provider.
Where 192.168.3.one. The gateway of the main provider.
Then everything will work again. over, only one appearance of sites is already easy to understand that we work through a VPN with an exit point in Germany.
detailed settings for a particular scenario go beyond this article and, as such, are no longer related to Wireguard settings. Wireguard itself in Routeros 7 is and works, while it is quite simple to set up, which we have just seen.
You can learn how to configure Mikrotik from scratch or systematize existing knowledge in an in.depth course in administering Mikrotik. The author of the course, the certified Mikrotik coach Dmitry Skoronov personally checks laboratory work and controls the progress of each of his students. Three times more information than in the vendor program of MTCNA, more than 20 hours of practice and access.
Setting Wireguard Client in Linux
Despite the fact that Wireguard has long been supported at the level of Linux nucleus with graphic tools for its configuration is not quite well, much depends on a particular distribution, but managing Wireguard from the command line is also very simple.
With Root or through SUDO, we will install and generate the keys just as we did on the server, then we will also create a configuration file:
Section [Interface] describes the network intese, in it we indicate the secret key key, the desired address in the VPN network and DNS server. The [Peer] section is responsible for connecting to the server, for all customers it is common, it contains a public server key, its address and port, as well as connecting and routing parameters.
To control the tunnel in manual mode, you can use the WG-Quick utility, to connect: Perform:
where WG0. The name of your configuration file, with the same name, a network intese will be created. If you run the command on behalf of an ordinary user, an increase in rights will be automatically requested.
At the same time, do not forget to add a section of the [Peer] section on the server and restart the service, for this you will need to indicate the public key of the client and its address, just like we did it for a Windows client.
You can learn how to configure Mikrotik from scratch or systematize existing knowledge in an in.depth course in administering Mikrotik. The author of the course, the certified Mikrotik coach Dmitry Skoronov personally checks laboratory work and controls the progress of each of his students. Three times more information than in the vendor program of MTCNA, more than 20 hours of practice and access.

How to configure Wireguard, your own VPN of a new century
Wireguard is a new, reliable and lightweight VPN protocol. We will consider the step-by-step procedure for setting up customers and Wireguard server in the cloud and on a home router to protect, for example, connecting to public Wi-Fi access points
We remind you that all the actions described in the article, the user makes at his own risk and risk. The material is given exclusively for introductory purposes. If you are going to reproduce the actions described below, we strongly advise you to carefully read the article to the end at least once. 3Dnews editors are not responsible for any possible consequences.
Wireguard is a modern protocol for the organization of VPN, written from scratch, free and with open sources. Unlike Mastodonts like OpenVPN or IPSEC, it is much simpler and easier. This also applies to the speed (translated) of the connection, and performance, and requirements for resources, and the settings process, and the volume of code. It was recently announced that Wireguard would be part of the future Linux nuclei, and later it will fall into all popular distributions, which indirectly indicates the maturity of this decision.
As stated in the announcement, we are considering a scenario for protecting the connection to public and other incredulous networks. Naturally, this use of Wireguard is not limited to. As an example, we consider the configuration of customers and the server (though in this case, these are conditional concepts. due to the specifics of the protocol), which works in the cloud and on the homemade Keenetic router. As practice shows, many public VPN services do not differ in scrupulousness in relation to customer data, so it is always better to have something of their own, controlled only by the user. In our case, we consider the installation and configuration of Wireguard, using a computer on Windows and a cloud virtual machine on Ubuntu for this.
We will need a complete set of Putty, so it’s better to download a MSI package with an installer immediately (available on the previous link), which will install everything and create a new group in the main menu. There we need Puttygen utility. After the launch, we generate a new pair of keys with default settings (RSA-2048), pressing the Generate button and leaving half a minute in the utility window. It remains to fill out several fields: in Key Comment you can enter the name of the key as a reminder, and in Key Passphrase and Confirm Passphrase enter the same password.
This password is still useful, so it must be remembered or saved in a reliable place. Next, in Puttygen, we save individually private (Save Private Key, File.PPK) and public keys. If you plan to use several cloud providers, then for each of them, and better for each server, use your own keys.
VSCALE is a cloud provider with its own sites and St. Petersburg and offering good configurations at low prices. The cheapest server whose capacities are quite enough for our tasks will cost 200 /month. Snopper storage costs another 40 /month. And it can also be transferred from one region to another. But there are no traffic restrictions.
Especially for readers, 3DNews VSCALE prepared a 3Dnews500 promotional code so that you can familiarize yourself with all the capabilities of the service. After registration, you need to replenish the balance by at least 100 or tie a bank card. Then the promotional code must be activated on this page. The code will be valid until 23:59:59 18.02.2020.
Service Interais is available in Russian. It’s easy to figure it out, so we will briefly describe the main stages. To work, first of all, you need to add a public SSH key received in Puttygen in the account settings. Then, in the server section, create a new server with Ubuntu 18 OS.04, indicating the desired region, tariff and key. Within a minute, the server will be ready and launched.
A separate SSH client is not required to access the command line, as VSCALE provides web console. For the entrance, enter the ROOT login and press Enter, then enter the following commands one by one and agree to everything by pressing Enter:
A couple of Комментарии и мнения владельцев in case of using other cloud providers. First, for Ubuntu 19.10 and more fresh versions of the OS do not need to add PPA, it will be enough for the first two teams. Secondly, access to the command line is possible using Putty. In the Host Name field, you need to enter the server IP address, and in the Connection → SSH → Auth section-the path to a private PPK key. Root login, and the password is the one that was indicated when creating the key (Key Passphrase). For convenience, you can save the session (Save). By pressing the Open button, the console window will open, at the first launch, preceded by a notification of security, with which we must agree.
Please note that even for the server turned off, resources are preserved, which are paid in the same way. Therefore, an unnecessary server must be deleted. If VPN is not necessary on an ongoing basis, but only sometimes, then you can save all the settings by creating a snapshot (backup). The snapshot itself can be transferred to another region and when creating a new server, choose it as a basis. It is necessary to create a snapshot strictly after completing the adjustment of the VPN server and very desirable in this case installation of the DDNS client, turning off the server immediately before creating a backup.
We set up wireguard on a desktop computer
Here we will consider the Wireguard setting on a desktop computer running the Ubuntu 20 operating system.04 or the like. If you use another operating system, then use the instructions from the Internet.
We repeat the commands that we have already used on the server:
Now, using a console text editor, we will create a file/etc/wireguard/wg0.Conf. The keys, again, need to be replaced with those that we generated. IP address 164.90.178.225 replace with your server address:
If you used a graphic text editor, then you need to protect the file clearly:
You can check the server work by the Sudo Wg Show command. The following information should appear on the screen (the keys and the port will differ):
You can find out your IP address with the next team:
He must coincide with the IP address of your server.
If IPV6 is configured on your server, then it will also work for you, even if your Internet service provider does not support it:
We set up Wireguard on Android smartphone
For smartphones under the control of the Android operating system, there is an official application from the original Wireard developer, available in the Google Play Store and, of course, for independent compilation from the source code.
The settings integration repeat the structure of the recovery configuration file that we already created earlier, but we will still give an example of filling the fields. Again, you need to replace the keys, the IP address and the server port on those that you generated.
- NAME: Any name
- Private Key: Siuobmwkwtxykugk0e2LDCLUVAMLUVAVKJRA/XBO7 // M4 =
- PUBLIC KEY: QMMAJIV5U5MYNOHZ6/B4ZQTUEURHAKKVQVMHCRWQ = (should appear automatically)
- Addresses: 10.73.105.3/32, FD41: CE44: B4C9: 44CA :: 3/128
- DNS Servers: 1.one.one.one
In the “Peer” section (you need to press the “Add Peer” button):
You can also generate a QR code with your configuration, which is convenient to read using the Wireguard application for a smartphone. To do this, create a wg0 configuration file anywhere.Conf similar to the one that we created for a desktop computer:
Now install the program for generating QR code and run it:
Count this QR code using the Wireguard application for smartphone. Do not forget to delete the configuration file after that, as it contains your private key:
After turning on the VPN, you can find out your IP address on the website https: // myip.com. He must coincide with the IP address of your server.
How to configure 1.one.one.one
Many users were left without access to the resources they need after blocking it.
Of course, you can not mess with the settings and try to use some other VPN. But with each month, the number of services that state locks do not apply to is less and less. It is in order not to stay at one point without access to the sites and applications you need, you should carry out this setting. In any case, I advise you to keep several different VPNs on the device.
So, in order to connect to WARP servers and use VPN, you must do the following:
- Download from Google Playy Wireguard.
- Download a special configuration for Warp.
- The file, by default, is downloaded to the “Download” folder. Using a standard file manager or application “Explorer” (the name depends on the manufacturer of your smartphone) go to the download folder.
- On most Android smartphones, the configuration downloads in the form of a text document with the extension txt. It is necessary to remove the extension through his renaming. When renaming, the system will swear that the file will become unavailable due to the removal of the format. Ignore this message, only “Warp should remain in the name.Conf “.
Do not forget to rename the configuration file.
Enter the necessary values into the indicated fields. This is necessary to connect to Cloudflare servers.
Everything, now you can use the old familiar service. In this case, Appendix 1.one.one.1 safely remove 1, as it is no longer required. All actions will be carried out strictly through the Wireguard application.
VPN for a separate application
Thanks to these actions, you will be able to return access to VPN.
Настройка WireGuard VPN на Android как настроить БЕЗЛИМИТНЫЙ и БЕСПЛАТНЫЙ ВПН на Андроид!
Separately, it should be noted the possibility of using this configuration only for specific applications. To configure the list of programs in which this VPN will be involved, you need:
- Open the Wireguard application.
- Click on the name of the configuration.
- In the upper right corner, press the pencil to go to the settings.
Constantly included VPN practically does not spend the battery.
Using these settings, you can leave a VPN constantly on and not worry about the need to include it when entering any applications. Many of us have unlimited traffic for various applications at the tariffs. So that the telecom operator when using such programs correctly takes it into account, and does not spend the main package, you have to constantly disconnect the VPN. If you configure the list of programs according to the instructions above, then there will simply be no need for this.
If you prefer to include VPN only if necessary, I advise you to add a switch to the control center so as not to constantly run the Wireguard application. On the example of Xiaomi smartphones:
Thanks to the switch, you do not have to keep the application running.
- Draw from the right upper angle down to call the control center.
- Press the “Edit” button in the upper right corner.
- Find the Wireguard application and click on the green “” in its upper right corner.
- Move the button to the convenient place of the center of control of the usual dragging.
After these actions, you can run a VPN directly from the control center. In general, I advise you to keep an additionally Adguard VPN on the smartphone. Without a speed limit, 3 GB of traffic is available in it, which is enough for many. But if it suddenly ends, you can simply change your account, and traffic will recover again.
Client setup WireGuard
On the computer from which you want to connect to Wireguard, it also needs to be installed. In Ubuntu and Debian, the installation team will look as follows:
In addition, if Resolvconf and Iptables packs are not installed in the system: they need to be installed:
After that, move the downloaded configuration file of the client Wireguard to the /etc /wireguard folder and rename it to WG0.Conf. The name of the configuration file should correspond to the name of the network intese that will be created Wireguard. For example:
sudo mv ~/wg0.client-losst.Conf/etc/wireguard/wg0.Conf
Or you can simply copy the contents of the file on the server and insert it into the local/etc/wireguard/wg0.Conf. The file is quite small, unlike OpenVPN. Now you can connect to the server using the WG-Quick command:
You can make sure that the virtual network is working by trying to kick the VPN server at internal address 10.66.66.one. You can also check that the Internet also works:
By default, the entire traffic of the client is redirected through the VPN server. This is configured in the client’s configuration file using the Allowedips directive. It indicates 0.0.0.0, which means all addresses, but you can change these settings and redirect only the desired traffic, or not at all redirect. You can see the wireguard connection condition with a team:
If you want Wireguard to connect to the server automatically after loading the system, you can add it to the Systemctl auto load:
Sudo Systemctl Enable Wg-Quick@WG0.Service
Sudo Systemctl Start Wg-Quick@WG0.Service
And the condition can be checked using the Status command:
Sudo Systemctl Status Wg-Quick@WG0.Service
Now you know how the customer customer is performed.
In this article, we examined how simple Wireguard settings in Linux are performed. As you can see, it is not necessary to deal with the intricacies of working with the program in order to install it on the server. According to my subjective sensations of the Internet with Wireguard faster compared to OpenVPN. And what vpn do you use? Write in the Комментарии и мнения владельцев!
The article extends under the Creative Commons Sharealike 4 license.0 When copying the material, the link to the source is required.