Unlock the iPhone to use accessories what to do
Why when you put the iPhone on charging writes an accessory is not supported
Often iPhones and iPads refuse to work with a particular accessory. In the article we will find out why when you put the iPhone on charging, the message “The accessory is probably not supported” appears, and try to solve this problem.
Since Apple is fighting the compatibility of its gadgets with the products of other companies, the main reason for the appearance of the message “This accessory is probably not supported” in the fact that the cable is non.Original. The remaining sources of the problem are more banal:
How the password protection system works in iOS, briefly
If you enter the wrong password 10 times, the device is blocked. After the first 5 attempts, you will have to wait 1 minute, then the time until the next input attempt will increase.
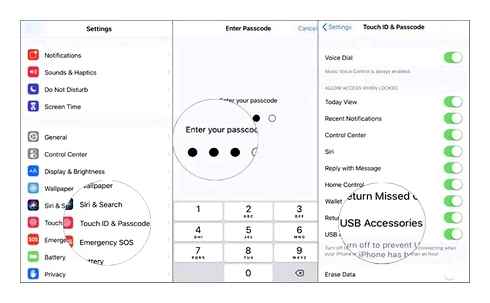
If you understand that the password is no longer remembered, Apple offers to erase all the data from the device. This is quite ok if you have a backup. About three simple ways to save data, read here.
Unlock iPhone with your Voice!!
You can delete a password with iPhone or iPad only using a computer. Apple Instructions. If there is no PC, you can contact an authorized service center or retail store, they will be provided there.
How to unlock the iPhone or iPad with one touch without pressing the home button (for iOS 13 and newer)
Go to the “Universal Access” section → “Home button”;
Activate the option “Open by applying a finger”.
Is it possible to unlock the iPhone 13, 12, 11, 10, Xs or XR by the face of her husband (wife) while he (she) sleeps?
To begin with, it is worth noting that the issue of authentication by unauthorized persons was affected by Apple presentation. The answer to it was also unequivocal: it is not possible to unlock the screen by the owner of the smartphone. In the case of the iPhone 13, 12, 11, iPhone X, XS or XR, the Face ID technology, which requires the presence of the owner of the device, will prevent authentication. At the same time, it will not work to unlock the gadget, even if you bring it closer to a sleeping person, because the user must definitely look at the smartphone during authentication.
The diagram of the process of unlocking the device is simple:
We remove the device from the sleeping mode.
The “sensor” of the sensor must necessarily be eyes, nose and ears.
It is not necessary to place the gadget strictly at the eye level, but it is still desirable not to remove from the field of face coverage with sensors. By the way, until the developers reported the boundaries of the sensors, but it is already clear that you should just keep a smartphone in the face for authentication.
Panicists who are afraid that during their sleep an unscrupulous friend or Partner will try to unlock the device, we inform you that this is impossible. In addition, Apple notes that even a qualitatively performed photo or mask depicting the owner of the device will not help to unlock. There is only one exception: if you sleep with open eyes. In this case, in case of fears, you can simply disable authentication via Face ID, but after that you will have to remove the lock by entering a password.
At the same time, those who wish to secretly explore the contents of someone else’s smartphone recommend not doing this, as this is a waste of time. To unlock the iPhone without its owner will not work. Either ask for access to the device from the owner of the gadget, or come to terms that this person has a guaranteed constitution to the right to inviolability of a private life.
On iOS 11.4.1 you can reset Lightning lock using a USB accessory
In iOS 11.4.1 Apple added Lightning locking function to prevent the police from breaking iPhones. If a person does not use a smartphone for a long time, then the Lightning connector is blocked and becomes affordable only after the owner entered the password or put his finger to the scanner. Thanks to this, a device like GrayKey became obsolete. But in fact, it turned out to be wrong.
Nevertheless, the researchers from Elcomsoft found a small loophole-if you connect any USB accessory to the iPhone, then the lock counter will be reset. However, this will only work if the smartphone has not yet moved into blocking mode.
We found that iOS is dropping a locking timer if you connect a USB accessory to the iPhone, which has never been associated with a phone earlier (in fact, accessories do not require interfacing at all). In other words, as soon as the police receive the iPhone, the employees need to immediately connect it to any compatible accessory to prevent port blocking. Note that this only works if the lock was not active before connecting the accessory.
Oleg Afonin
Elcomsoft
Afonin says that you can use the Lightning to USB adapter, which is in the Apple 39 store, but with an adapter with Lightning for 3.5-mm so can not be done. Now Elcomsoft is testing other accessories, including third.Party ones, to see which of them drop the Lightning lock timer.
Lightning to USB adapter
Most likely, this is not a serious vulnerability, but Apple’s error. Nevertheless, this means that the police can still gain access to any iPhone and continue to use GrayKey.
Not so long ago, Wispear showed The Spearhead 360 van, capable of breaking down devices on iOS and Android at a distance. The company reports that this truck uses unobvious holes in the safety of systems. However, while these machines are not common, since they are very expensive-3.5-5 million.
Vulnerability in access restriction mode
I’ll make a reservation right away: I am unknown (I can’t tell ”, but really unknown) vulnerabilities that use CELLEBRITE and GRAYSHIFT to detour restrictions. I can only make assumptions on information received from public sources. The first assumption is the vulnerability in Lightning. Remember, I mentioned the adapter from the Lightning connector to exit 3.5mm for headphones? It is this adapter that does not obey the general rules: its connection does not discard the Tiere of activation of the protective regime, and if the protective mode has already turned on, you can connect and use this adapter without unlocking the iPhone.
Meanwhile, unlike many similar adapters with USB Type C using USB Alt Mode to transmit an analog signal, this adapter is a full digital device with a built.In chip of DACs. That is, even in the “protective” mode, the iPhone nevertheless transfers some data through a seemingly tight-block port. And what if our device “introduces” the adapter for activating the port, and then he will go along the vulnerabilities chain? This is just an assumption, but the option seems quite plausible.
The second assumption is again the vulnerability of Lightning, but a little on the other side. Recently it turned out that another Apple adapter. Lightning adapter. HDMI, is actually a computer with the built.In Secure Boot and Darwin’s core. Over, this adapter does not have its own firmware; The firmware on it is pumped from the iPhone every time the user connects the adapter. In this case, the firmware is not signed by a unique identifier, the digital signature is static. It is unlikely that the vulnerability was found in this adapter, but the idea seems quite promising.
Finally, there are also “universal access” devices that can be used by visually impaired, people with fine motor skills and other categories of users who need special devices for communication with iPhone. This category of devices has a special status; According to Apple, their use leads to deactivation of restricting access to accessories. You can try to present an attack in which our device will first be presented by an adapter for 3.5mm (data exchange went), after which. An accessory for people with violations of fine motor skills (in other words, external keyboard).
Why do I think that vulnerability lies precisely in the Lightning protocol? In the black market, you can find both “engineering” models of different iPhone versions, in which some of the hardware of protection are deactivated, as well as certain special cables that provide additional functions. A detailed article in English came out about this; Here is a Russian.Speaking article referring to it. And here they posted a photograph of a special engineering cable. Alas, without details. Plus in detail about Lightning as a whole, you can read here.
Limited USB access mode on iPhone and iPad: what is it and how to configure correctly?
You can get access to iOS device using several ways, including through USB. For example, through the Lightning connector, the cracker can load all the necessary data from the iPhone (or iPad), hack access code and unlock the device.
The “USB limited access mode”, which appeared in iOS 12, turns off the charging and transmission of data through Lightning, if more than an hour has passed since the last unlock iPhone or iPad. That is, even having got the device, the attacker will not be able to withdraw data from him through USB if enough time has passed since his last unlock.
The regime is activated by default, but there may be circumstances in which you would like to disconnect it. For example, to charge a phone from a computer’s computer or for the duration of Carplay on long distances, when you cannot unlock the iPhone for a long time.
How to unlock the iPhone without password. There are as many as 8 ways
There is no perfect protection. There are only different degrees of reliability. This also applies to iPhone.
Recently, we explained how important it is to have a digital-letter password of locking, and not a standard 6-cerenticial in iOS. But this is only the top of the iceberg, and under it. A real hardcore.
We tell you how the methods of blocking iPhone are bypassed and whether it is possible to protect yourself from this.
Disclaimer: This article is not designed to help unlock the stolen iPhone. You can test all the methods described below at your own peril and risk.
How the password protection system works in iOS, briefly
If you enter the wrong password 10 times, the device is blocked. After the first 5 attempts, you will have to wait 1 minute, then the time until the next input attempt will increase.
If you understand that the password is no longer remembered, Apple offers to erase all the data from the device. This is quite ok if you have a backup. About three simple ways to save data, read here.
You can delete a password with iPhone or iPad only using a computer. Apple Instructions. If there is no PC, you can contact an authorized service center or retail store, they will be provided there.
Password protection in iOS is worse in dfu mode
DFU (Device Firmware Update). A special mode that gives access to the engineering menu allows you to restore the firmware, etc.D. Focus is that DFU has no restrictions on the number of password entry attempts.
Thus, if you set the goal, you can choose the code and unlock the smartphone. If you are too lazy to enter numbers manually, you can buy a gadget for an auto.Transmission for 500 (already cheaper). But there are more professional systems, they are much more expensive.
Let’s see how professionals do it. For educational purposes, of course.
How to go around Face ID
When the Face ID just appeared in the iPhone X, it was full of holes in it. Apple claimed that even twins would not bypass the person recognition system.
But something went wrong. Face ID sometimes took children for their parents. And one customer twice returned the smartphone to the store. He stubbornly confused her with a colleague. In general, the system was uncomfortable and unsafe.
BKAV Vietnamese company spent only 150 to create a Face ID mask. The basis was printed on a 3D printer, the nose was made of silicone, eyes and mouth were printed and glued to the layout.
Soon it was fixed. But in August 2019 they found an even more funny way to unlock. Tencent researchers have shown how to deceive Face ID with ordinary glasses and islands.
If your iPhone is activated on your iPhone, the smartphone regularly checks whether you look at the screen. But if you are wearing glasses, then Face ID will not read 3D information in the eye area. The system believes that there are black areas with white dots.
So, if you sleep or have lost consciousness, then your smartphone will be easy to unlock. Specialists simply glued squares of islands with spray dots in the middle of the glasses and put them on a “sleeping” colleague. And his iPhone was successfully unlocked.
How fake fingerprints
The Touch ID system has drives the digital prints of prints and keeps hashs in the protected area Secure Enclave, separated from the main storage.
How To Jailbreak iPhone On Passcode Or iPhone Disabled (Unlock iPhone To Use Accessories)
When you are trying to block the iPhone using a print, Touch ID checks a new code with data from Secure Enclave. And the decoding of the fingerprint is stored in RAM and only immediately after scanning.
Of course, it is much cooler than scans-pictures in certain folders (this sinned by some Chinese devices). But the first.Generation Touch ID could be deceived using a sheet of paper with 2400 dpi prints printed. If you have an iPhone 5s, try, it may work.
Over: the print can be removed directly from the screen. And not only unlock the iPhone with the old scanner, but also prohibit the real owner to wash the data from him.
With more new models is more difficult. We need a 3D printer and material that the smartphone will take for human skin. And a fairly accurate 3D fingertip. And a limited number of attempts.
Anil Jane’s biometric identification expert and his colleagues from the University of Michigan have developed a technology for the production of such “fake fingers” from the electric current of silicone composition and pigments. Fakes had the same mechanical, optical and electrical properties as the fingers of real people.
Formally, the technology was supposed to improve the reliability of scanners. But it all depends on whose hands it would be.
Other researchers, having only a good photo of the German Minister of Defense Ursula von der Layen, made his 3D model. They shot not a finger separately. The fingerprint was shown from a high.Resolution picture.
The minister agreed to participate in the experiment. Result. She herself proved that the method really works.
How to access the only message
Cyberexperts Natalie Silvanovich and Samuel Gross from Google Project Zero showed how the vulnerability of CVE-2019-8641 provides access to passwords, messages and e-mail. And also allows you to turn on the camera and the microphone on the iPhone.
Project Zero is engaged in the search for vulnerabilities in Google products and its competitors. Experts said: if you know the victim’s Apple ID, just send the victim a message configured in a special way.
The iOS has a built.In ASLR technology, which complicates the operation of some vulnerabilities. It changes the location of important data structures in the address space of the system: for example, stack, heaps, loaded libraries, images of executable files.
Silvanovich and Gross found a way to get around aslr. Using this and other five vulnerabilities found, experts achieved the execution of arbitrary code on the iPhone. In the black market, about 10 million would be paid for information about these bugs.
Good news: the main and most complex vulnerability of CVE-2019-8641 closed to iOS 12.4.2 in September 2019. Bad: how many more such holes there are, no one knows. But statistics are not happy.