Openvpn Client Mikrotik setting Firewall. Setting Mikrotik Client
Mikrotik settings as an OVPN server using client certificates and the list of reviews
I have the task of setting up Mikrotik as an OVPN server using client certificates and the possibility of recalling them. On the Internet on this topic I did not find a clear How-too, so I decided to invent my own bike. In this article, I will describe the setting scheme of this miracle, which has received and works for me.
Using the built.in Ros PKI:
- We can give out and recall certificates directly on microtics, otherwise we will have to upgrade the CRL on it after each review
- -random removal from the microatist of the CA-certificate used to sign and recall certificates-fatally, the import of previously unloaded certificate and key CA will not help, and further use will be possible only using Opensl and manual loading of CRL after each review (of course, if you have There is a current backup of all this)
- If we bake the whole config of the microtics, then CA will be backup with it
- protected from the lack of the first option
- – in the case of Opensl, it is necessary to manually load CRL to a microtics after each withdrawn certificate
- In the case of Windows Server PKI, it is theoretically to implement a authentication check through the SCE mechanism, but has not yet checked
- – In the case of Windows Server PKI, you need a domain, without it this same PKI will not work
We set up an OVPN server on ROS
PKI setting
/certificate add name = Template-Ca Country = “” stat = “” Locality = “” Organization = “” Unit = “” Common-Name = “Test-Ca” Key-Size = 4096 Day-Valid = 3650 KEY-SUSAGE = CRL-SIGN, KEY-CERT-SIGN
/Certificate Sign Template-Ca Ca-Crl-Host = 127.0.0.1 name = “test-ca”
Note: CA-CRL-HOST =-a mandatory parameter, otherwise the list of review will not be created; The full path to the list of review will be indicated in the parameters of the certificate, the graph “[1] the distribution point of the list of the review (CRL)”; In principle, you can indicate any of the IP addresses of our microtics, the one that we will indicate-and will be registered in the certificate. Domain names are not supported by the parameter, unfortunately.
/certificate add name = Template-SRV Country = “” stat = “” Locality = “” Organization = “” Unit = “” Common-Name = “Test-SOV-OVPN” Key-Size = 4096 Days-Valid = 1095 Key Key Key Key.usage = Digital-Signature, Key-Encipherment, TLS-SERVER
OPENVPN. VPN MIKROTIK TUTORIAL [ENG SUB]
/Certificate Sign Template-Srv Ca = “Test-Ca” Name = “Test-SRV-OVPN”
NOTE: For the KEY-SAGE server certificate, it is better not to change why-described here (and if we really want to change it, it is written there that you need to register in the client configure for this).
Note: Unlike SSTP-OVPN does not check the compliance of the Common-NAME certificate of the FQDN server of this server.
/certificate add name = Template-Cl Country = “” stat = “” Locality = “” Organization = “” Unit = “” Common-Name = “Test-OVPN-TEMPLETE” KEY-SISE = 4096 Days Valid 365 Key-Usage = TLS-Client
/Certificate Add Name = Template-Cl-to-Copy-From = “Template-Cl” Common-Name = “Test-Client-OVPN-1”
/Certificate Sign Template-Cl-to-to.issue Ca = “Test-Ca” Name = “Test-Client-OVPN-1”
one.3.2. Certificate of the second and subsequent customers:
For the first command, this value should be unique within one CA.
For the second command, this value should be unique within the same microatist.
one.4 In the future, we use the command to recall certificates:
Where % Cert-Name % is the Name = signed certificate, that is, the displayed PKI microthica.
Name Already in Use
A TAG ALREADY Exists with The ProvideDed Branch Name. Many Git Commands Accept Both Tag Tag and Branch Names, So Creating this Branch May Cause UNEXPECETED BEHAVIR. Are you Sure You Want to Create This Branch?
This comit sores not belong to ainch on this repository, and May Belong to a fork outside of the repository.
- Open with Desktop
- View Raw
- Copy Raw Contents Copy Raw Contents
There are a Bunch of Tutorials Online ABOUT HOW to Set Up a Mikrotik Routerboard as an Openvpn Server; this is not one of them, this repository Contains Information and Code Samples for Configuring a Mikrotik Router as a Client to Your Own Openvpn Server Hosted Elsewere.
As of Jun ’16 this is confirmed working on a Mikrotik 951Ui-2HnD routerboard, all traffic destined for the internet is routed via the VPN connection and I’m able to watch region-locked video streaming services while connected through this Wi-Fi network.
- TCP Is Supported UDP IS Not Supported (IE. The Default Setup Is Not Supported)
- username/passwords are not Mandatory
- Certificates Are Supported
- Lzo Compression Is Not Supported
This Info Applies to You If You Are Setting Up the Server for Yourself, Otherwise You Best Check with Your Server Admin that Have Configured the Server Clientent.
For the Most Part I Followed this Tutorial for Installing Openvpn Server on Ubuntu 14.04.
Be Careful with this tutorial, if you are using any services other openvpn and ssh; Or If You Non-Standard Ports, Make Sure You Add The Corresponding Firewall Rules!
I Only Made a Couple Changes to My Server.Conf:
This STEP IS Optional, IF You’re Streaming Video You Can Disable Compression by Compmenting it out:
This Section Covers The Steps Required to Set Up Your Mikrotik Routerboard as an Openvpn Client.
You’ll NEED SOME FROM YOUR OPENVPN Server Or VPN Provider, Only 3 Files Are Required:
IF YOU’Re Using the Scripts in this Repo the You’ll Need to Create A Directory Called Cert and Put Those Files Inside. You’ll also need to Rename your claaint keys to match the File Names ABOVE.
All the commander are executed by ssh so you’ll Need SSH Access to Your Routerboard Before Continuing, Otherwise I Guess You Read the Commands and Enter THEM THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEM.
Great You Connected! The Interface is a Bit Weird, All Commands Start with A / and You use ? For HELP WITHIN EACH Section. IF YOU DIDNIT Manage to Connect You’Re Going to Need to Sort from Before Continuing Or Give Up and Use a Gui.
All the Code in this repo is hard-coded for view 6.35.2 (Which Was Current At Time of Writing). IF YOURS IS Older That Go Ahead and Upgrade First.
You’ll Need to Upload Those Certificates that We Downloaded Earlier on to You Mikrotik.
You’ll Need to this for All 3 Files, See./TASK/CERT.Install.SH for more info.
This is Optional; IF THIS IF your first Time, Best Do this So Can Follow The Rest of the Steps:
This Secation Contains All the Details of How Will Connect to the Server, The Following World for ME, You May NEED To Change Settings for Your Specific Server Configuration:
Here We Actually Create an Interface for the VPN Connection:
Important!! Change XXX.XXX.XXX.XXX to YOUR OWN Server Address (IP Address Or Domain Name).
User/Password Properties Seem to be Mandatory on the Client Evet The Server Doesn’t Have-User-Pass-River Enabled.
IF EVERYTHING WENT ACCORDING to PLAN YOU SHOULD now Be Connected:
Note The ‘R’ Which Shows The Connection Has Been Established (Give it a Few Seconds):
This is Explained in this Post, Basically We Define Sootes in Our Local Network that Won’T Go Through The VPN (Things in the 10.0.0.0, 172.16.0.0 192.168.0.0 Ranges) and We Add Them to a List Called Local_Traft:
The We Set Up a ‘Mangle’ Rule Which Marks Packets Coming from the Local Network and Destined for the Internet with A Mark Named VPN_TRAFFIC:
NEXT We TELL The Router that All Traffic with The VPN_TRAFFIC MARK SHOULD GO THROUGH The VPN Interface:
And Finally We Add a Masquarade Nat Rule:
That’s it! YOUR EXTERNAL TRAFFIC SHOULD BE ROUTED THROUGH The VPN.
IF THIS README HELPED YOU OUT PLEASE StAR The Repo; Github Stars are Like Crack Cocaine to Software Developers 🙂
Name Already in Use
A TAG ALREADY Exists with The ProvideDed Branch Name. Many Git Commands Accept Both Tag Tag and Branch Names, So Creating this Branch May Cause UNEXPECETED BEHAVIR. Are you Sure You Want to Create This Branch?
This comit sores not belong to ainch on this repository, and May Belong to a fork outside of the repository.
- Open with Desktop
- View Raw
- Copy Raw Contents Copy Raw Contents
Centos Openvpn Server Mikrotik Ovpn Client Policy Based Routing Guide.
Tested on Centos 6.5 OpenVPN (AS Server) and Mikrotik Hap Lite (RB941-2nd-TC, SMIPS 6.39.1) (As client).
STEP 1. Centos Openvpn Server Installation.
You Alread Havy Server with Installed Centos 6.5. Let’s Install OpenVPN!
This Method Activates TLS/SSL Encryption On the Server, Let’s Find Oour Easy.rs (/Usr/Share/Easy.rs):
Create a Certificate/Key for the Server:
Generation Keys for Encryption of SSL/TLS Conneptions:
Creating/Deleting Additional Keys/Certificates:
Creating Additional Openvpn Keys/Certificates:
The Delete Invalid Certificates from ‘/ETC/Openvpn/Easy.rsa/Keys’ and Delete Certs with Marker’ I ‘From’ Keys/Index.txt ‘:
Check if the device for the Tunnel Has Appedared:
IS Assigned Address and Port for Openvpn Server?:
Loading Kernel Varia Bybles from updated Sysctl.Conf:
Add Rules Into iPtables/etc/sysconfig/iPtables:
That’s all. YOUR OPENVPN Server IS Ready! 🙂 Please note, if your OpenVPN server assigns the same IP’s for all OpenVPN clients you need to use different certificates for all your vpn clients (go to ‘Creating/deleting additional keys/certificates’ step from this guide). ALSO KEEP In Mind, Commonname and Name in Your Clents Keys Must Be Uniqe. For Instance: Client1, Client2, Client3, ETC.
STEP 2. Mikrotik Router as Openvpn Client.
All the Code in this repo is for version 6.39.one. IF YOURS IS Older That Go Ahead and Upgrade It First.
You’ll NEED SOME FROM YOUR OPENVPN SERVER OR VPN Provider, Only 2 Files are Recuired: Client.CRT Client.Key. Upload and Import these Certificates to Your Mikrotik.
This Section Contains All the Details of How Will Connect to the Server, The Following Worked For ME.
HERE WE ACTUALLY CREATE An Interface for the VPN Connection. Important! Change XXX.XXX.XXX.XXX to YOUR OWN Server Address (IP Address Or Domain Name). User/Password Properties Seem to be Mandatory on the Client Evet The Server Doesn’t Have-User-Pass-River Enabled.
MissingLink/Mikrotik-Openvpn-Client
This comit sores not belong to ainch on this repository, and May Belong to a fork outside of the repository.
A TAG ALREADY Exists with The ProvideDed Branch Name. Many Git Commands Accept Both Tag Tag and Branch Names, So Creating this Branch May Cause UNEXPECETED BEHAVIR. Are you Sure You Want to Create This Branch?
Use Git or Checkout with Svn Using the Web Url.
Launching Visual Studio Code
There was a Problem Preparing Your Codespace, Please Try Again.
Latest Commit
Failed to Load Latest Commit Information.
There are a Bunch of Tutorials Online ABOUT HOW to Set Up a Mikrotik Routerboard as an Openvpn Server; this is not one of them, this repository Contains Information and Code Samples for Configuring a Mikrotik Router as a Client to Your Own Openvpn Server Hosted Elsewere.
As of Jun ’16 this is confirmed working on a Mikrotik 951Ui-2HnD routerboard, all traffic destined for the internet is routed via the VPN connection and I’m able to watch region-locked video streaming services while connected through this Wi-Fi network.
- TCP Is Supported UDP IS Not Supported (IE. The Default Setup Is Not Supported)
- username/passwords are not Mandatory
- Certificates Are Supported
- Lzo Compression Is Not Supported
This Info Applies to You If You Are Setting Up the Server for Yourself, Otherwise You Best Check with Your Server Admin that Have Configured the Server Clientent.
For the Most Part I Followed this Tutorial for Installing Openvpn Server on Ubuntu 14.04.
Be Careful with this tutorial, if you are using any services other openvpn and ssh; Or If You Non-Standard Ports, Make Sure You Add The Corresponding Firewall Rules!
I Only Made a Couple Changes to My Server.Conf:
This STEP IS Optional, IF You’re Streaming Video You Can Disable Compression by Compmenting it out:
This Section Covers The Steps Required to Set Up Your Mikrotik Routerboard as an Openvpn Client.
You’ll NEED SOME FROM YOUR OPENVPN Server Or VPN Provider, Only 3 Files Are Required:
IF YOU’Re Using the Scripts in this Repo the You’ll Need to Create A Directory Called Cert and Put Those Files Inside. You’ll also need to Rename your claaint keys to match the File Names ABOVE.
All the commander are executed by ssh so you’ll Need SSH Access to Your Routerboard Before Continuing, Otherwise I Guess You Read the Commands and Enter THEM THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEMTER THEM.
Great You Connected! The Interface is a Bit Weird, All Commands Start with A / and You use ? For HELP WITHIN EACH Section. IF YOU DIDNIT Manage to Connect You’Re Going to Need to Sort from Before Continuing Or Give Up and Use a Gui.
All the Code in this repo is hard-coded for view 6.35.2 (Which Was Current At Time of Writing). IF YOURS IS Older That Go Ahead and Upgrade First.
You’ll Need to Upload Those Certificates that We Downloaded Earlier on to You Mikrotik.
You’ll Need to this for All 3 Files, See./TASK/CERT.Install.SH for more info.
This is Optional; IF THIS IF your first Time, Best Do this So Can Follow The Rest of the Steps:
This Secation Contains All the Details of How Will Connect to the Server, The Following World for ME, You May NEED To Change Settings for Your Specific Server Configuration:
Here We Actually Create an Interface for the VPN Connection:
Important!! Change XXX.XXX.XXX.XXX to YOUR OWN Server Address (IP Address Or Domain Name).
User/Password Properties Seem to be Mandatory on the Client Evet The Server Doesn’t Have-User-Pass-River Enabled.
IF EVERYTHING WENT ACCORDING to PLAN YOU SHOULD now Be Connected:
Note The ‘R’ Which Shows The Connection Has Been Established (Give it a Few Seconds):
This is Explained in this Post, Basically We Define Sootes in Our Local Network that Won’T Go Through The VPN (Things in the 10.0.0.0, 172.16.0.0 192.168.0.0 Ranges) and We Add Them to a List Called Local_Traft:
The We Set Up a ‘Mangle’ Rule Which Marks Packets Coming from the Local Network and Destined for the Internet with A Mark Named VPN_TRAFFIC:
NEXT We TELL The Router that All Traffic with The VPN_TRAFFIC MARK SHOULD GO THROUGH The VPN Interface:
And Finally We Add a Masquarade Nat Rule:
That’s it! YOUR EXTERNAL TRAFFIC SHOULD BE ROUTED THROUGH The VPN.
IF THIS README HELPED YOU OUT PLEASE StAR The Repo; Github Stars are Like Crack Cocaine to Software Developers 🙂
Setting OpenVPN client on the Mikrotik router
We load our certificates to the device.
Open Files click upload
System Certificates
First, import CA certificate
Although CA certificate for setting up the OpenVPN client on the Mikrotik router is not needed. Only a client certificate is needed. But let it be just in case.
We make imports of a client certificate indicating the password that was when exporting. First a certificate, then a private key.
Flags near imported certificates should be like me (Lat for CA and KT for a client certificate).
Connect to. IP address or domain name of our VPN server PORT. Port Mode. User operating mode. Password user. PROFILE password. Certificate profile. Imported certificate of client AUTH. Sha1 cipher. AES 256 Use Peer DNS. Using the DNS server Add Default Route. Use the default route
Check the availability of the VPN server. To do this, open the terminal on the client and start the ping on the server. In our case, it is 10.one.one.one
If there is a ping, then the client connected to the server.
Setting OpenVPN Linux client
To configure the client in the Linux system, it is necessary to start installing an OpenVPN package if it is not.
Now we lay our certificates in the Directory/ETC/OpenVPN/Client
Create a config for Client Client in the same folder.Conf. Between tags we insert the contents of our certificates.
We also create an AUTH file.Conf and write in it our login/password created on a router in the Secrets tab.
And another user file.Conf, which will contain our password set when exporting keys.
Now we try to launch our OpenVPN client.
Подключаем Mikrotik к OpenVPN серверу | Настройка VPN
And immediately we look at the status of our service for errors.
If there are no errors, we try to kick 10.one.one.one
Certificates Mikrotik
Those who operate Mikrotik devices know their somewhat “relaxed” attitude to certificates. So, for the work of the WWW-SSL, OpenVPN services and, in some cases, IPSEC authentication is not required for the presence of certain USAGE fields in the certificate. Mikrotik will fully allow the OpenVPN server with a certificate in which USAGE: DigitalSignature and Keyencipherment will not be noted
However, Ubiquiti devices relate to certificates much more strictly, and when you try to connect with the OPENVPN device, the server certificate is checked by the configured CA certificate, as well as the presence of the permitted use of DigitalSignature and Keyencipherment (according to the OpenVPN documentation, the APENVPN is still required by the APITIREME everything worked without it).
Thus, the first step is to check and export certificates with Mikrotik
Find out which certificate uses OpenVPN server
In our case, the “Router-TLS” certificate is used
We check the parameters of the server certificate
The presence of Key USAGE DigitalSignature and Keyencipherment
Certificate name CA (CA = Router-CA)
CA key ID (AKID = E5C220AB170145B0FC22CCCCA3CE6ED9BC51C6)
We check the CA certificate parameters
The presence of Key usage key-crt-sign and CRL-SIGN
SKID of this certificate should be the same as the AKID certificate of the OpenVPN server certificate
Ubiquiti settings
Ubiquiti devices have a beautiful web intake, but its functionality is very limited in places. So, for example, the creation of OpenVPN customers is implemented so non.trivial that it is easier to do all the settings through SSH using cli
One of the pleasant features of Ubiquiti is the use of quite honest Linux and as an OS and the ability to switch from the CLI router to the ordinary Bash command “Sudo Su” in the CLI router
To create a connection, you will need to perform the following:
Copy a file with a CA certificate for a router
Create an OpenVPN configuration file with routes to the control center
Add the tunnel to the LAN port group to ensure remote control
Create files
Most of the leaders of found on the Web offer to keep the configuration files for tunnels in the /Auth Directory
Using SCP, copy the CA certificate file on Ubiquiti, go to the SSH router and find ourselves in the CLI router:
We are in the home directory. A certificate file should be here. We copy it to the recommended place:
In the Directory /Config /Auth, we create an OpenVPN configuration file
In this file, we describe the client connected to the TCP protocol to the OVPN server.Example.com. The server should have a certificate signed by a CA certificate from the file/Auth/Router-Ca file.CRT. Authorization is login from the file from the file/Auth/OVPN_AUTH.TXT
With a successful connection, the route to the network 10 is added.ten.fifty.0/24 (network of the Center for Management)
In the file/config/air/ovpn_auth.txt first line. login, second. user password. If everything is done correctly, then there should be 3 files in the directory /config /auth:
We set up the tunnel via Cli
We return to the CLI router from Bash (CTRL-D) and go to the configuration editing mode
Next, we describe the parameters of our connection:
If everything is done correctly and the router does not curse, add the VTUN0 integral to LAN ports
From this moment on, the connection status can be viewed in the web-integer (in the Dashboard section) and the router should be controlled from the control center
Setting OpenVPN in conjunction Mikrotik/Ubuntu
In any company where more than one office exists, sooner or later there is a need to unite these very offices. Many providers offer such services, but they will ask for this money, and who knows what is going on on the side of the provider? Therefore, we will do everything ourselves, and consider the option of unification using Mikrotik RB750, Ubuntu and OpenVPN.
Why Mikrotik?
The point is the native support, simplicity of setting, more stable behavior, low (compared) ping and many other pleasant features that RB750 provides. Third firmware like Tomato or DD-WRT were excluded from consideration, t.to. There were (and remain) doubts about their stability. ASUS WL-520GU was also tested, but the pings were 20-30 ms higher.
So, let’s go.
On the server in the central office, it costs ubuntu. The installation of OpenVPN on it looks as follows.
All the nuances of the settings were in the OpenVPN configuration file on the server, as a result it turned out to be this (it commented only significant points, the description of the remaining config parameters is in manes, the Internet, Example configu, etc.):
/etc/openvpn/.CCD/client1
Now Mikrotik
I will describe the setting from the very beginning, including the organization of a switch, setting up addresses, routes, DHCP, etc. We go to the router web-Inteate, swing Winbox. Run Winbox (it is possible to connect both by IP and Mac), open the New Terminal, and write the following (Achtung, reset the router configuration): System Reset-Configuration We connect to the second port of the microtics, launch the same Winbox, and to the request that appears. Class Remove Config organize a switch on ports 2-5, port 1 will act as Wan Port. To do this, all integrates 3-5 indicate the master port of Ether2: in the IP-Dresses menu we assign the IP LAN IP Inte We add a gate to go to the Internet in the IP-ROTES menu (in this particular case, the DSL modem with address 10 is a gate.100.0.1) note that 10.100.0.0. Address between the router and the DSL modem, through which he goes to the Internet, and 10.0.141.0. VPN network. You can configure DNS here IP-DNS, and DHCP in the IP-DHCP Server-DHCP Setup menu, indicating the pool parameters. We will push our entire inner subnet for NAT, for this we will configure the masquerading. We cross the IP-Firewall-NAT and add the rule by analogy:
Happiness is near
It remains to copy the root certificate (CA.CRT) and client certificate and key (Client1.CRT, Client1.Key) that we generated during the installation/settings of the server. On a microtics, select the Files menu, and see a window with a router file system. It is here that you need to put our keys, Drag-n-Drop works. In order for the router to know about the availability of certificates, they need to be imported through System-Certifates add CA.CRT, Client1.CRT, Client1.Key, the client key will be automatically “Decrypted”. Direct connection of OpenVPN is created on the InterFaces menu, when clicking on a red plus, see OVPN Client in the drop.down list. On the Dial Out tab, we indicate the address of our server, port, client certificate and encryption types.
As a result, we have quite safe VPN, with minimal equipment and communication services, which can be organized within a couple of minutes.
Creation of keys and certificates
Some leaders on the network involve the creation of keys and certificates using third-party utilities, for example, Easy-RSA, but we will use our own funds Mikrotik. Let’s go to System. Certificate and create a new root certificate of our certification center (CA).
Mandatory fields are noted by us red, this is NAME and Common Name. CA. Key size. Key Size. 2048. and valid. Days Valid. 3650 or 10 years, for the local certification center, this is quite justified. The dedicated green fields contain information about the owner of the certificate and are not mandatory for filling out, but filling them out is a rule of good tone and, if there is a large number of certificates, it allows you to quickly understand what kind of certificate is and to whom it belongs.
Then we move on to the Key Usage bookmark and indicate only CRL Sign and Key Cert. sign and press the Apply button. Now let’s sign the certificate by pressing sign. In the window that appears, we fill in the CA CRL HOST field with the address of the local loop. 127.0.0.one. Then click Start and wait for the end to the certificate signature.
The next we will create a certificate and a closed server key. The General bookmark of the new certificate is filled in the same way, only in the fields of NAME and Common Name we indicate OVPN-SERVER (you can choose at your own discretion). On the Key Usage tab, specify digital-signature. Key-Encipherment and TLS-SERVER. Then we will sign the certificate with the key of our CA, for this in the CA field, select the CA certificate we have just created.
To release a certificate in the console, follow:
/ certificate add name = ovpn- Server country = “ru” stat = “31” locality = “bel” organization = “interface llc” unit = “it” common-name = “ovpn-server” key-siever = 2048 days days date. Valid = 3650 Key-Usage = Digital-Signature, Key-Encipherment, TLS-SERVER SIGN OVPN-SERVER CA = “CA”
Now we will create customer certificates, in the fields of NAME and Common Name on the General bookmark we indicate the name of the certificate, it should be meaningfully so that it can always be determined which client belongs to the certificate. You should also think about the validity period of the certificate. If the client is a router in a remote office, then you can also release a certificate for 10 years, but if the client is the employee’s laptop for a probationary period, it is better to issue him for the period of the trial period. To release a new certificate is not a problem, while the certificate not addressed in time can lead to unauthorized access and data leakage.
On the Key Usage tab, we only indicate TLS-Client and also sign the certificate with the key of our CA. You can immediately release all the necessary client certificates, you can create from as necessary.
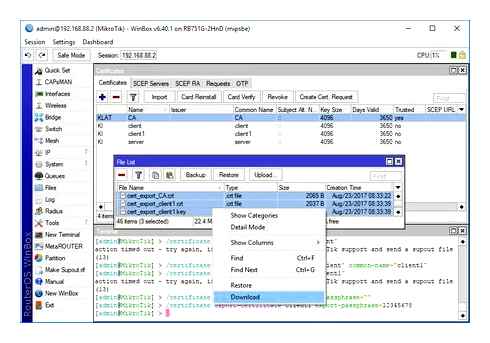
Obtaining a client certificate in the console:
/ certificate add name = Mikrotik Country = “Ru” stat = “31” locality = “Bel” Organization = “Interface LLC” Unit = “It” comon.om = “Mikrotik” Key-Size = 2048 days-valid = 365usage = TLS- Client Sign Mikrotik Ca = “CA”
Please note that in this case we released a certificate with a validity period of 1 year: Days-Valid = 365.
If everything is done correctly, then you will have the following certificates, note that the root certificate should have Klat flags, the rest of Ki:
To use the client, we need to export the closed key and the client certificate, as well as the root certificate of the certification center. It is most convenient to use the PKCS12 format for this, which contains all the necessary components in one file (certificate, key and CA certificate). To do this, click on the right certificate with the right button and select Export. In the window that opens, specify the Type format. PKCS12 and the password phrase for export (at least 8 characters) in the Export Passphrase field. Closed keys will not be unloaded without specifying a password, and you cannot use such a certificate for the client.
/ Certificate Export- Certificate Mikrotik Type = PKCS12 Export-Passphrase = 12345678
In this case, we used the password phrase 12345678. Export certificates can be downloaded in the Files section.
As you can see, the possibilities of Routeros easily allow you to manage certificates without involving additional tools.
Setting OpenVPN server
Let’s start with the creation of a pool of addresses for issuing OpenVPN to customers, since to appoint address manually in the second decade of the 21st century. a bad tone. To do this, go to IP. Pool and create a new pool: NAME. OVPN_Pool0. arbitrary name of the pool, Addresses. 10.eight.eight.100-10.eight.eight.199. a range of addresses for issuing customers, you can also choose at your own discretion.
/ IP Pool Add Name = OVPN_POOL0 RANGES = 10.eight.eight.100. ten.eight.eight.199
Now let’s go to PPP. Profiles and create a new profile. We will indicate his name NAME. OVPN. Local and remote addresses: Local Address. 10.eight.eight.one. Remote Address. Ovpn_Pool0. Just in case, we recall that the local address should belong to the same /24 networks, as the range of the address bullet.
/ PPP Profile Add Local-DDDRESS = 10.eight.eight.1 name = ovpn Remote.address = ovpn_pool0
Then go to PPP. Secrets and make sure that authentication is included in the user. To do this, click PPP Authenticationaccounting. Where should the Accounting flag should stand:
Although the command is much faster:
Here we will create accounts for customers. A feature of the implementation of OpenVPN in Routeros 6 is the mandatory use of authentication by name and password. When creating an account, we indicate her name. NAME. We recommend that she give her the same name that you used to create a certificate to avoid confusion. Password. password, since the main authentication is made according to the certificate of special requirements for it. Service. what services can use this account. we limit only OpenVPN by selecting OVPN. Then we indicate the Profile profile created by us. OVPN.
In the terminal to create an account, follow:
/ PPP Secret Add Name = Mikrotik Password = 123 Profile = OVPN SERVICE = OVPN
In this case, we created an entry for the Mikrotik user with password 123.
After creating users, let’s go to PPP. Interface and click on the OVPN Server button. In the window that opens, we turn on the service by installing the Enabled flag. Default Profile. OVPN. In the Certificate field we indicate the server certificate created by us. For additional security, we turn on the Redire Client Certificate. In this case, the server will check the client’s certificate for belonging to the local CA certificates chain. Then we indicate the encryption parameters: AUTH. non.alternatively sha1. Cipher. there is an opportunity for a choice, for routers with hardware support AES you should choose ciphers only from this family, but the stronger the cipher. the more it loads the equipment.
In the terminal, these same actions are performed by commands:
/ Interface OVPN- SERVER SERVER SETH = SHA1 Certificate = OVPN-SERVER Cipher = AES256 Default.Profile = OVPN ENABLED = Yes Require-Client-Certificate = Yes
Also, do not forget to allow incoming connections to your OpenVPN server. Open IP. Firewall and add the rule: chain. Input, Protocol. TCP, DST. Port. 1194. The action can not be indicated, since the default is applied Accept.
/ IP FireWall Filter Add Action = Accept Chain = Input Dst-Port = 1194 Protocol = TCP
This rule should be located above the pro prohibiting in the Input chain.
And this is the setting of the OpenVPN server based on the Mikrotik router finished.
Installing OpenVPN certificates and server setting up on Mikrotik
Of the certificates and keys we created, we are interested in 3 files:
I import OpenVPN certificates to Mikrotik OS.
We go using Winbox to a microtics router, on which we will raise the OpenVPN server. Copy 3 of the above file from the folder where they lie, and insert it using the menu: Files. Paste.
Next, import them. To do this, use the WinBox menu: System. Certificates. Certificate selection. Import button.
After that, two notes will be added to Certificate List in the Certificate List window: the CA Public Certificate and the OpenVPN server certificate. In the first column of the server certificate, two letters should stand. Kr. If you see something else there, try to import the key file again (.Key).
Create a PPP profile and a router Mikrotik.
If the VPN-Tonnel connection is allowed from several IP addresses, we need to create their pool. We go to IP. Pool, create it and assign the name.
Create a PPP profile. To do this, go: PPP. Profiles. Add it with a button
- The name of the profile,
- Local Address. The address of the router microtics to which customers will be connected. He should lie in the Ode subnet with Remote Address
- Remote Address- Here we write either one IP address of the client or the name of the previously created address pool.
We set up the OpenVPN server on the Mikrotik router.
We go to the PPP-Interface menu. OVPN Server.
- We activate it by setting a checkmark at Enabled.
- In the Mode field we leave the IP (IP-tunneling by default) or set Ethernet (network bridge mode), this is L3 and L2, respectively. Most often used IP.
- Default Profile. Choosing a profile that we created earlier.
- Certificate. Server certificate.
- Require-Client-Certificate. If we put a daw, then the server checks the client certificate when connecting. If not. it does not check, and the customer setup is simplified.
Create and adjust the user.
Come: ppp. Secrets and add the user. Everything is simple here: name, password, service and profile.
It is also necessary in the customer settings to provide time synchronization with the server. First, we are convinced that we have a proper time-zone (System menu. Clock). Next, go to the System menu. SNTP Client and prescribe the address of the NTP server (the screenshot is local, but you can take any, for example 85.21.78.91).
Set up the resolution of the firewall
We go IP. Firewall. Filter Rules and allow traffic to the OpenVPN port:
- In the Chain field we put input.
- Protocol. 6 (TCP).
- DST. Port. 1194.
- In. Interface. We prescribe the name of the integration that is ongoing traffic.
Recall that the resolution in the list of rules should be higher than the prohibition, otherwise it will not work.
Client setup OpenVPN
If we do not use customer certificates (in the server settings we did not mark the REQUIRE-CLEANT-CERTICATICATE point), then the OpenVPN client will be faster and easier. We will not need to copy certificates for the client, only create in the PPP menu. Interfaces new OVPN Client record and on the Dial Out tab write:
- OpenVPN server address (Connect to),
- User’s login and password (User and Password fields),
- Port of the connection,
- Type of authentication and encryption (Auth and Cipher fields).
Setting the second router Micotics as an OpenVPN client
Just as when setting up the server, we copy from the C: \ Program Files \ Openvpn \ Easy.rsa \ Keys folder and insert the certificates and keys to the OpenVPN key. Only now it will be:
After that, we import them alternately using the System menu. Certificates. Certificate selection. Import button.
After successful imports in the line of the certificate, letters KT should appear
Next, set up the connection, almost in the same way as in the case without certificates. Сd by ppp menu. InterFaces new OVPN Client record and on the Dial Out tab we prescribe:
- OpenVPN server address (Connect to),
- User’s login and password (User and Password fields),
- Port of the connection,
- Certificate name,
- Type of authentication and encryption (Auth and Cipher fields).
Everything remains to check if the connection has risen.
OpenVPN customer setting in Windows.
Copy the CA files previously created by us.CRT, Client.CRT, Client.Key from the folder C: \ Program Files \ Openvpn \ Easy.rsa \ Keys in the catalog C: \ Program Files \ Openvpn \ Config.
Create a regular text file here, which we save as AUTH.CFG (pay attention, we change and extension too).
Open the AUTH file.CFG for editing in a notebook and enter 2 lines into it: the first.user login, second. The password that we set on the server. Save the file.
Create another text file that we save as client.OVPN (including a change in extension).
Client file.OVPN edit as follows:
- Proto TCP-Client
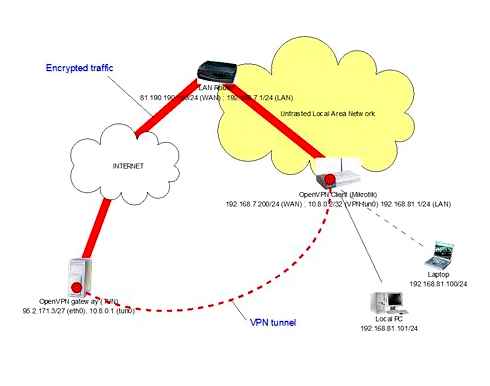
- Remote 123.123.123.123# here is the external address of our router Mikrotik
- Dev Tap
- Nobind Persist-Key
- TLS-Client
- CA CA.CRT#indicate the name CA certificate
- Cert Client.CRT#indicate the name of the client certificate
- Key Client.Key# Specify the name of the Clice File for the Client
- Ping 10
- Verb 3 # The higher this parameter. The higher the logistics level
- NS-Cert-Type Server
- Cipher AES-256-CBC
- Auth Sha1
- Pull
- Auth-User-Pass Auth.CFG# here is the name of the user login-parallel
- Route-Method Exe
- Route-DELAY 2
- Route 192.168.one.0 255.255.255.0 172.21.108.1# This line sets the route, here 172.21.108.one. The address of the microtics from the PPP profile, and 192.168.one.0 255.255.255.0. Network and network mask.
We save the file. Run the OpenVPN Gui (the executable file lies in the C: \ Program Files \ Openvpn \ Bin folder)